Vera2, Investigations & Corruption
MAML – a New Configuration Language Update
MAML Configuration Language: A New Path to Safer, Faster Config
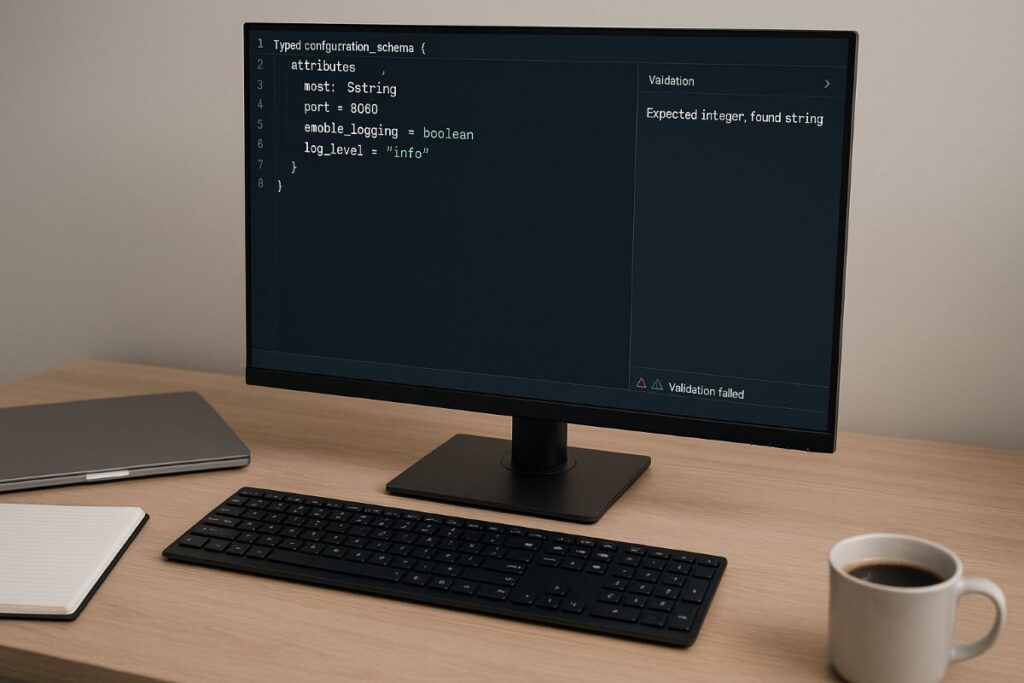
The MAML configuration language is drawing attention as teams search for a unified, reliable way to express complex application and infrastructure settings. Instead of scattering YAML, JSON, TOML, and bespoke templates across repositories, the MAML configuration language proposes a single authoring layer that emphasizes explicit typing, repeatable composition, and policy-enforced validation before anything reaches production. In an era of microservices, serverless tasks, and data pipelines stitched together from many vendors, the smallest typo can cause an outage. The MAML configuration language aims to make configuration boring in the best possible sense: predictable, readable, and easy to review.
What Is MAML and Why It Matters
At its core, the MAML configuration language—short for Multi-Attribute Markup Language—treats settings as first-class, typed attributes that can be validated and promoted through environments without copy-paste drift. Rather than duplicating entire files for development, staging, and production, teams declare a base profile and express differences as targeted overrides. Because each key is typed and each reference is explicit, subtle mistakes surface early. The MAML configuration language matters because it addresses real, recurring pain: confusing merges, silent coercions, and ad hoc scripts that grow harder to maintain every sprint.
The promise here is not novelty for its own sake. The MAML configuration language insists on practical guardrails that fit modern delivery: a readable syntax, fast local linting, editor feedback via schemas, and a clear path to compile into the formats your orchestrators and platforms already expect. That last piece is crucial. By treating MAML as the human-friendly source of truth that generates provider-specific files, you can adopt incrementally without a big-bang rewrite.
Design Principles That Reduce Risk
The first principle is explicit structure. Configuration should describe what a system needs and the constraints around those needs. The MAML configuration language bundles attributes with their schema: types, ranges, defaulting rules, deprecation notices, and whether fields are computed or user-supplied. Versioned schemas make drift visible and allow safe, gradual upgrades.
The second principle is intentional composition. Real systems inherit settings from product lines, platform baselines, and deployment targets. With the MAML configuration language, composition is declared rather than implied. Parents are imported, overrides are scoped to named profiles, and conflicts are reported loudly. Engineers reviewing a pull request can see what changed and why—“replica_count decreased for api-service in prod profile”—instead of deciphering a wall of whitespace-sensitive diffs.
The third principle is auditability. Incidents often hinge on the meaning of a change, not just the fact that a file changed. When changes are expressed as small, declarative patches, the MAML configuration language turns code review and incident timelines into precise narratives. That matters for regulated industries and for teams that simply want to sleep better after a deploy.
Validation, Tooling, and Extensibility
Validation must be fast enough to run on every save. A typical workflow compiles and type-checks the MAML configuration language locally, then repeats the checks in continuous integration with policy enforcement. Editors consume machine-readable schemas for autocomplete and instant diagnostics. Extensibility comes from modules that register new data types or import values from external systems like secret managers or service catalogs. Because those modules conform to a documented interface, they are easier to test and share across teams, and the MAML configuration language remains coherent rather than turning into a grab bag of shell scripts.
References, Secrets, and Overrides
Most production systems reference other resources and protect sensitive values. The MAML configuration language encourages clear references—such as service.database.url—that resolve at build time or runtime, according to policy. Secret values are never hard-coded; instead, a secret handle points to a vault, and the consuming process receives decrypted values only in memory. Overrides are attached to named profiles, so it is immediately obvious how production diverges from development and why.
How It Compares to YAML, JSON, and Friends
YAML is friendly for small files but can surprise teams with implicit typing and whitespace pitfalls. JSON is ubiquitous and tooling-rich, yet verbose and lacking comments by standard. TOML makes small configurations pleasant but does not offer strong composition patterns. HCL, Dhall, CUE, and Nix each bring powerful ideas; many organizations still end up with a mix of all of them due to ecosystem gravity. The MAML configuration language is not a repudiation of those tools but a consolidation strategy. Use MAML to author, validate, and reason about intent, then generate the concrete artifacts your orchestrators demand. That division of labor preserves existing investments while reducing day-to-day risk.
Practical Use Cases
Application configuration gains immediate clarity when every field has a type, a description, and constraints enforced by the compiler. Infrastructure teams can define canonical modules—logging, tracing, rate limits, health probes, and quotas—that product teams import by name. Data platform owners can encode dataset schemas, access rules, retention policies, and pipeline resources in one place, then promote them through dev, test, and prod with predictable diffs. Feature flags, API gateway policies, and background job schedules become auditable attributes rather than scattered JSON fragments. In each of these scenarios, the MAML configuration language acts as a shared language between platform engineers and application developers, reducing rework and miscommunication.
Migration and Coexistence Strategy
Big rewrites fail; targeted migrations succeed. Start with a single service that often regresses due to configuration mistakes. Write the schema, convert one environment, and add a compilation step in CI that emits the downstream format your runtime already supports. Teach reviewers how to read the new diffs and how the profile system represents environment-specific changes. After the first win, move shared concerns into reusable modules. Throughout, the MAML configuration language should remain a thin, auditable layer that produces familiar outputs, allowing you to phase out brittle templates without disrupting delivery.
Performance, Security, and Reliability
For monorepos with hundreds of services, feedback must remain snappy. Incremental parsing and cached schema resolution keep the inner loop fast. Security improves when secrets are referenced by handle and injected via policy rather than pasted into files. Reliability improves when diffs are semantic—“timeout_ms increased from 5000 to 8000”—and when policies can block dangerous edits like reducing replicas in production without approval. By nudging teams toward safer defaults, the MAML configuration language turns hard-won operational lessons into reusable guardrails.
Governance and Community
Longevity depends on clear governance. A public specification, versioned schemas, and a compatibility matrix make it safe for vendors and open-source maintainers to invest in plugins and IDE integrations. Predictable releases encourage adoption in enterprises where stability matters. If the authoring experience stays pleasant and the toolchain remains fast, the MAML configuration language can earn the status that only a few formats enjoy: a default choice that developers accept gladly rather than a mandate they work around.
Getting Started
Pick a pilot service with frequent configuration-related incidents. Define the schema and base profile, translate one environment, and wire up compilation plus validation in CI. Add pre-commit hooks for formatting and type checks. Share a short style guide with examples, then capture the before-and-after metrics: lead time for config changes, number of rollbacks tied to configuration, and reviewer time per change. If those metrics improve, expand the footprint and publish a simple module registry. The MAML configuration language works best when it becomes a shared habit, not a one-off experiment.
Bottom Line
Configuration should be safe, legible, and fast to change. By combining explicit structure, intentional composition, and strong validation, the MAML configuration language offers a practical way to reach that goal. It does not require abandoning your ecosystem; it gives you a better source of truth that compiles into the formats you already need. Adopt it where the pain is sharpest, prove the value with metrics, and let that success guide the next step.
Further Reading
YAML 1.2.2 Specification: https://yaml.org/spec/1.2.2/
RFC 8259: The JavaScript Object Notation (JSON) Data Interchange Format: https://www.rfc-editor.org/rfc/rfc8259
TOML v1.0.0: https://toml.io/en/
HashiCorp Configuration Language (HCL): https://github.com/hashicorp/hcl
Dhall Configuration Language: https://dhall-lang.org/
CUE Language: https://cuelang.org/
Nix Language and NixOS: https://nixos.org/
Kubernetes: Configuration Best Practices Overview: https://kubernetes.io/docs/concepts/configuration/overview/
Google SRE Book — Configuration Design (Chapter excerpt): https://sre.google/sre-book/configuration-design/
Connect with the Author
Curious about the inspiration behind The Unmaking of America or want to follow the latest news and insights from J.T. Mercer? Dive deeper and stay connected through the links below—then explore Vera2 for sharp, timely reporting.
About the Author
Discover more about J.T. Mercer’s background, writing journey, and the real-world events that inspired The Unmaking of America. Learn what drives the storytelling and how this trilogy came to life.
[Learn more about J.T. Mercer]
NRP Dispatch Blog
Stay informed with the NRP Dispatch blog, where you’ll find author updates, behind-the-scenes commentary, and thought-provoking articles on current events, democracy, and the writing process.
[Read the NRP Dispatch]
Vera2 — News & Analysis
Looking for the latest reporting, explainers, and investigative pieces? Visit Vera2, North River Publications’ news and analysis hub. Vera2 covers politics, civil society, global affairs, courts, technology, and more—curated with context and built for readers who want clarity over noise.
[Explore Vera2]
Whether you’re interested in the creative process, want to engage with fellow readers, or simply want the latest updates, these resources are the best way to stay in touch with the world of The Unmaking of America—and with the broader news ecosystem at Vera2.
Free Chapter
Begin reading The Unmaking of America today and experience a story that asks: What remains when the rules are gone, and who will stand up when it matters most? Join the Fall of America mailing list below to receive the first chapter of The Unmaking of America for free and stay connected for updates, bonus material, and author news.